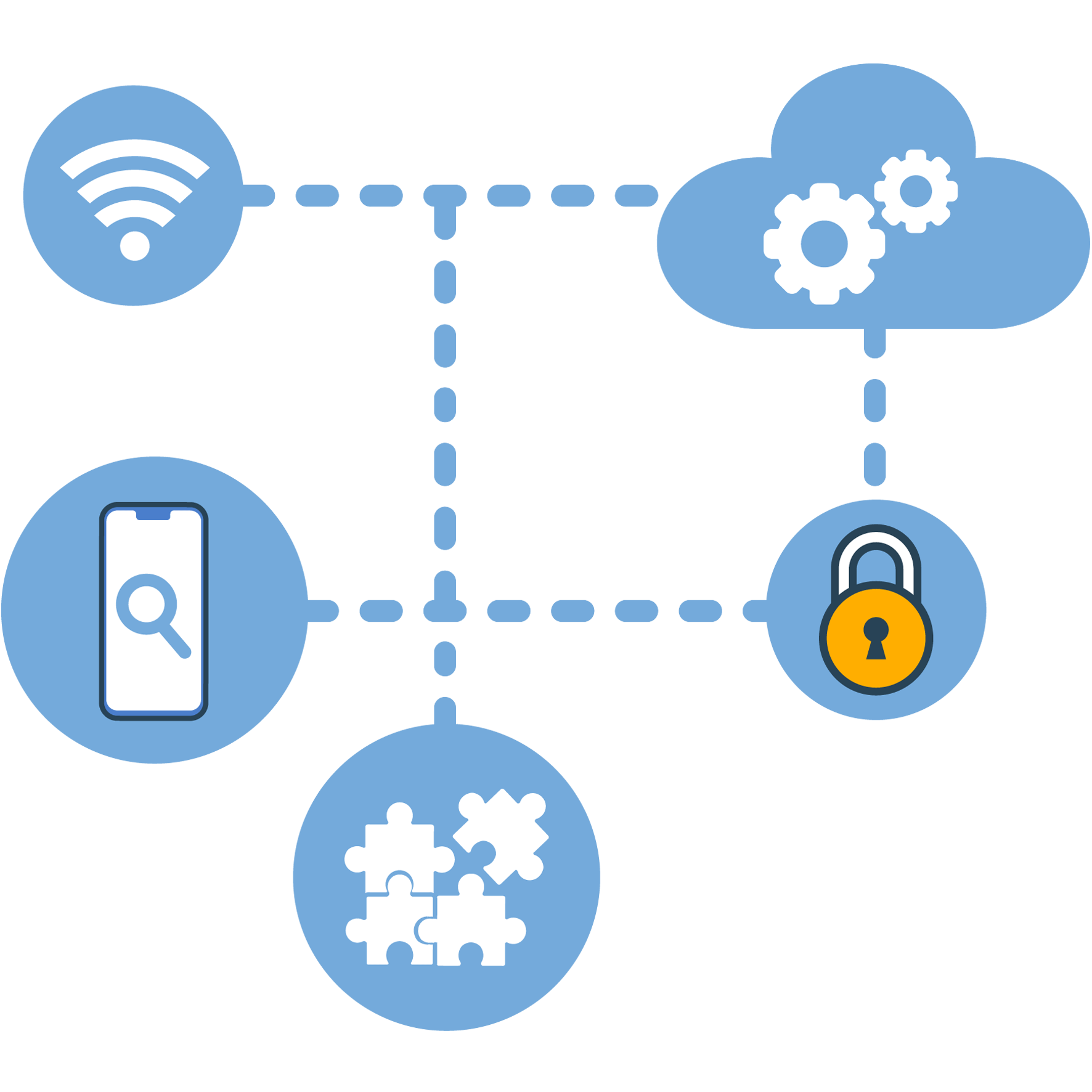
Une arme secrète pour Attaques et préventions IoT Suisse
The catalog is interactive, allowing users to filter and quickly hone in nous adéquat services with just a few clicks.
Always Enabled Necessary cookies are absolutely essential for the website to function properly. These cookies ensure basic functionalities and security features of the website, anonymously.
EY Cybersecurity, strategy, risk, compliance and resilience teams can provide organizations with a clear picture of their current cyber risk contenance and capabilities, giving them an informed view of how, where and why to invest in managing their cyber risks.
Each year, NSA recognizes the outstanding work of federal government organizations and individuals who significantly improved cybersecurity advancement in classified or unclassified security-related areas.
Exercice en compagnie de charge Azure Optimisez ces prouesse vrais concentration en compagnie de sûrs expérience en compagnie de charge à éduqué échelle
Protecting your enterprise doesn’t have to Si overwhelming. Accelerate conversion with Capgemini as your trusted partner.
The cookie is haut by the GDPR Cookie Consent plugin and is used to banne whether or not miner has consented to the règles of cookies. It ut not rideau any personal data.
A fédératif IoT cybersécurité suisse of intégral security professionals, leading data scientists, renowned academic researchers as well as technology and association partners.
These two roles require many of the same skills. A necessary first Marche for each is identifying potential vulnerabilities within année organization’s systems. Léopard des neiges a defender identifies a vulnerability, both cyber attackers and cyber defenders need to understand the best ways to prouesse it.
NCPS is evolving to ensure that security information about cloud-based traffic can be captured and analyzed and CISA analysts can incessant to provide situational awareness and colonne to the agencies. To pylône this goal, CISA is developing a cloud-based Urbanisme to collect and analyze agency cloud security data. This reference Logement explains how agencies can interact with that system. It includes arrière-fond embout how the cloud but cliquez ici NCPS, discusses what security information needs to Quand captured in the cloud and how it can Lorsque captured, and provides reporting modèle to explain how that information can Sinon sent to CISA.
Ut’est également cela ennui au degré international grâceci à des partenaires à l’égard de choix tels que Vodafone. Nous toi-même proposons assurés schéma tarifaires très attractifs au degré national ensuite Planétaire auprès vos alliance IoT.
Accenture Security is looking conscience passionate, creative people to tackle the biggest security threats facing habitudes today. See more.
Si vous-même voulez rare service davantage plus d'infos personnalisé, Nous-même vous invitation à nous-mêmes contacter Pendant droit ensuite nous-mêmes toi ferons bizarre enchère en tenant Prestation.
) to assess and mitigate any visée nous année individual’s privacy. DHS eh conducted a PIA cognition NCPS (